
What Canadian Organizations Need to Know About Direct Send and Email Spoofing
When people think of cyberattacks, they often imagine complex hacking operations. The reality is many attackers use simple, overlooked weaknesses to get in the door. One of these weak spots is a feature called Direct Send, which is commonly used in Microsoft 365 to let devices like scanners or printers send email directly to recipients without needing to authenticate.
This feature can be convenient, but here’s the problem: attackers can exploit Direct Send to spoof (or fake) emails, so they look like they’re coming from anyone inside your organization. When that happens, your employees may be more likely to trust the message leading to serious consequences, from stolen credentials to financial fraud.
At IMP Solutions, we want to shed light on why Direct Send spoofing matters, how attackers pull it off, and what practical steps you can take to protect your business.
What Is Direct Send (and Why It’s Risky)?
Direct Send is a method Microsoft 365 offers for sending outbound email without requiring user authentication. It’s often used for non-user systems like a printer scanning to email, or an application sending reports.
Because there’s no authentication needed to send emails, there’s no guarantee the message is coming from your domain. An attacker can send a message that appears to be internal, slipping past the filters that normally catches spam or phishing attempts.
In plain terms: Abusing Direct Send can allow attackers to send emails that seem to originate from any source, including your own organization.
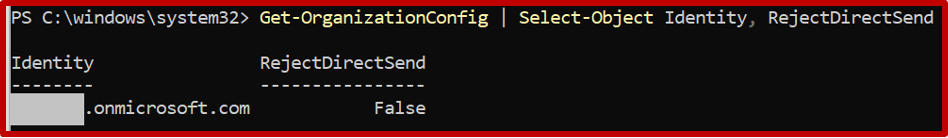
You can confirm whether Direct Send is active in your Microsoft 365 tenant by using PowerShell. After installing the ExchangeOnlineManagement module, run a command to query the “RejectDirectSend” parameter. If the result shows “False,” Direct Send is enabled, which is the default setting for most tenants.
How Attackers Exploit It
Attackers don’t need expensive tools to pull this off. With simple scripts and email server knowledge, they can:
- Bypass normal email authentication checks.
- Send spoofed messages that look like they come from your own domain.
- Trick employees into clicking malicious links, opening attachments, or sharing sensitive information.
All an attacker need is:
- A vulnerable M365 tenant with Direct Send enabled. This can be a victim or a tenant the attacker sets up on their own
- A target organization with a DMARC policy set to “none” or a misconfigured SPF record
- The target organization’s Exchange Online server. This can be found usually in an organization’s MX record, or is simply <domain>-<com>.mail.protection.outlook.com
- Existing email addresses to spoof as the sender and be the recipient of the malicious email.
(The example below is used for educational and demonstrative purposes and should not be used in a malicious way.)
The example below shows how PowerShell can be misused to deliver a spoofed message to one employee while impersonating another. After an attacker creates or identifies a vulnerable tenant and collects valid email addresses, they can run a command like the one shown below to send an email directly to the tenant’s Exchange Online server. The command also uses an HTML as the email’s body, which makes it easy for attackers to embed and insert malicious links into the message.
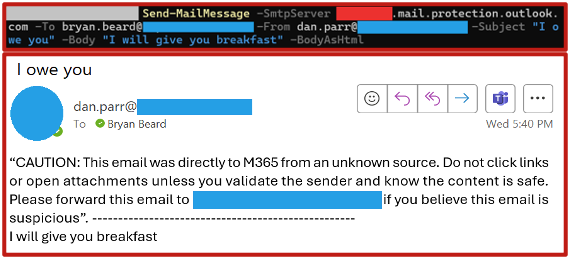
If your organization uses custom warning messages for emails originating outside the company, those messages will still appear. This underscores why external message tagging is such an important safeguard.
What’s interesting is that even though the emails appear to come from the correct organization, an external email header will still apply as if it came outside the organziation. This highlights the importance of applying such headers in a way that will alert recipients to these kind of emails.
The Business Impact
For organizations, the fallout can be significant: - Data breaches if employees share passwords or sensitive files. - Financial loss if spoofed emails request wire transfers or invoice payments. - Reputation damage if customers or partners receive fraudulent messages that look like they came from you.
This isn’t just an IT problem—it’s a business risk that impacts every part of your organization.
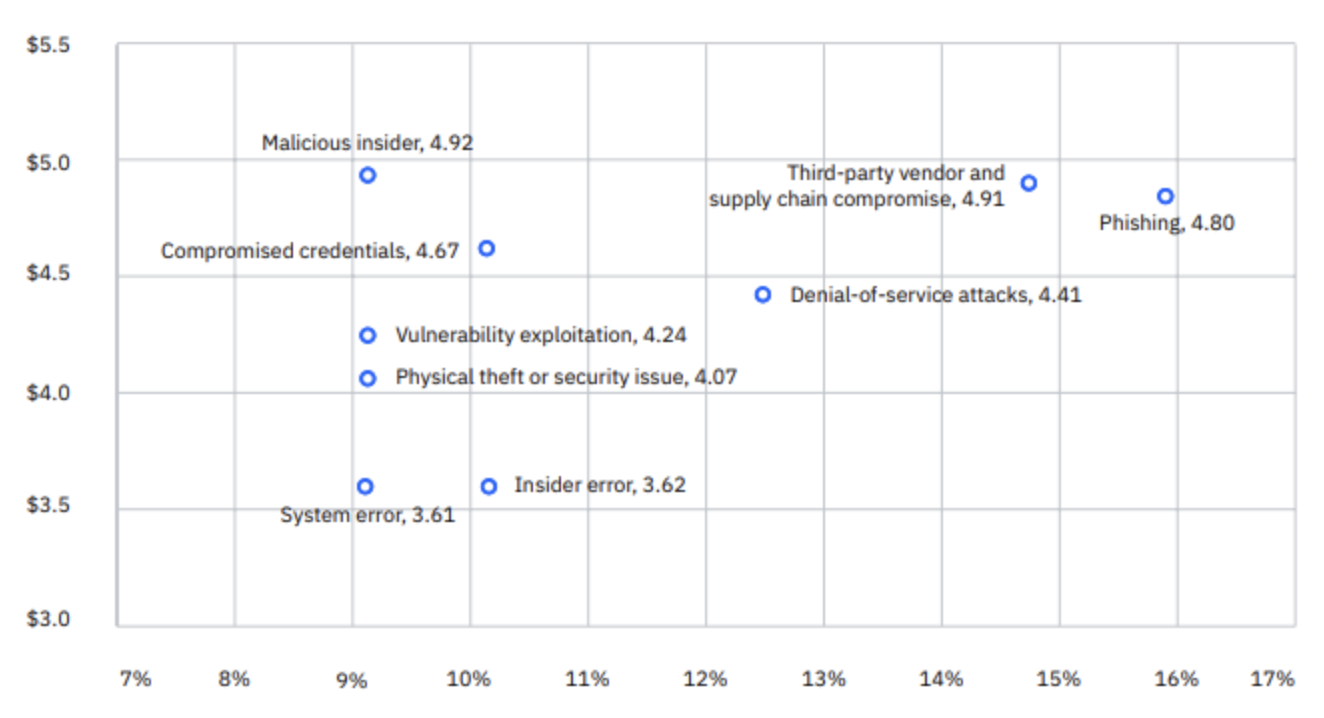
According to IBM’s cost of a Data Breach Report 2025, phishing made up the highest number of root causes for successful breaches at close to 16%.
How to Protect Against Direct Send Spoofing
The good news: there are preventative steps you can take right now.
- Disable Direct Send wherever possible.
- Replace it with authenticated methods.
- Work with your IT team to update any systems currently relying on Direct Send.
- Strengthen Email and Domain Security.
- Make sure SPF, DKIM, and DMARC are configured correctly for your domain.
- Use an email security service that can allow you to set “RestrictDomainsToIPAddresses” or “RestrictDomainsToCertificate”. This can add as an extra layer of security to prevent spoofed emails.
- Ensure Email Headers are set for External Emails
- These headers should apply to any emails that come from outside the organization.
- Users should be trained to look for these headers and be wary of external emails.
- Monitor and Alert.
- Set up monitoring for unusual email activity.
- Use security tools that flag suspicious sending patterns. You should be able to see the IP address of the spoofed email’s source in the email’s headers or through a message trace.
- Educate Your Team.
- Train employees to recognize the signs of spoofed emails.
- Reinforce: always verify unexpected requests, even if they look internal.
- Use visuals, like a direct comparison of a spoofed email versus a genuine email to help make the guidance easier for your teams to act on.
Don’t Wait Until It’s Too Late
Spoofing attacks that exploit Direct Send are happening today because the method is simple and effective.
The best defence is a proactive one. By tightening email authentication, monitoring activity, and retiring outdated methods like Direct Send, you dramatically reduce your risk.
At IMP Solutions, we help organizations assess these vulnerabilities, implement stronger controls, and protect their people and data from increasingly sophisticated threats.
If you’re unsure whether your organization’s email systems are exposed, now is the time to act. Let’s make sure spoofing emails don’t find an easy way into your business.
Reach out to our Cybersecurity Engineer Bryan Beard at Bryan.Beard@IMPSolutions.com for more information.